Several reports comparing figures for the current year to 2023 indicate that the number of ransomware attacks has increased compared to all of last year. It is currently one of the most dangerous and damaging threats to organizations of all sizes. This malicious software, created to encrypt data and demand a ransom in exchange for its release, has advanced in complexity and has become increasingly common, severely affecting the operability and security of institutions. However, one of the key factors facilitating the success of ransomware attacks is social engineering, a manipulation technique that exploits people's trust to gain unauthorized access to systems and data.
Social engineering relies on deception, exploiting human vulnerability to carry out attacks that often bypass conventional security measures. From phishing emails to more sophisticated hoaxes, attackers employ a variety of tactics to dupe victims and spread ransomware. This symbiotic relationship between social engineering and ransomware has not only amplified the magnitude of these attacks, but also increased their impact and complexity.
This paper explores how social engineering and ransomware intertwine to form a powerful threat. The fundamentals of both techniques and their interconnection in a real attack will be examined. In addition, current data and strategies to mitigate the risk will be presented, providing a comprehensive view of how to deal with this growing threat.
The Art of Deception and Coercion
Social engineering has become one of the most sophisticated and dangerous techniques in the world of cybersecurity. This practice is based on manipulation, persuasion and deception targeting the most critical components of a system, the users who administer and use them on a daily basis.
Ransomware, meanwhile, is a form of digital extortion that has gained notoriety for its ability to cripple entire businesses in a matter of minutes. This type of attack has evolved into a business model known as Ransomware as a Service (RaaS), where ransomware developers rent out their malicious software to other cybercriminals, allowing even those with few technical skills to carry out devastating attacks.
To understand how RaaS has incorporated social engineering into its service, it is necessary to review which of all its techniques are the ones that could benefit it.
• Phishing: An attacker impersonates a trustworthy entity through emails or messages to deceive the victim and obtain sensitive information such as passwords or personal data.
• Spear Phishing: Variant of phishing that specifically targets an individual or organization, using personalized information to increase the chances of success.
• Smishing: Phishing through SMS messages, where malicious links or requests for information are sent under the guise of a trustworthy sender.
• Baiting: The attacker offers an incentive or "bait", such as an attachment or an infected physical device (USB), for the victim to open it and execute malware.
• Pretexting: The attacker invents a credible scenario or pretext to trick the victim into divulging private information or performing a specific action.
• Vishing: Phishing through telephone calls, where the attacker impersonates a legitimate entity to deceive the victim and obtain confidential information.
• Quid Pro Quo: Technique in which the attacker promises a benefit in exchange for information or access, such as promising to solve a technical problem in exchange for access credentials.
ABeing a business model that needs to be profitable, for RaaS, incorporating this type of techniques allows them to save time and money. Since the value of acquiring a zero-day vulnerability is usually very high or exploiting some kind of backdoor could take more time than required. If we consider the principles of social engineering-such as the desire to help, the inclination to accept flattery, and the difficulty of saying 'no' in the work environment-it is not so illogical to think that techniques such as spear phishing, vishing, and baiting, for example, can be effective.
In terms of the methods associated with ransomware cyberattacks, we usually speak of a situation in which coercion is used, which is exercised through threats to force someone to act in a certain way, in order to obtain money or other benefit. This dynamic is called extortion, and its aim is for the cyberattacker to get what he or she wants, usually money. There are currently four methods of extortion, which escalate in consequences depending on how the victim reacts:
• First, initial extortion occurs when cyberattackers encrypt all files, and victims must pay to regain access to the original unencrypted data.
• Double extortion occurs when some or all of the data is stolen and they threaten to reveal or sell it if the ransom is not paid.
• Triple extortion occurs when the two previous methods do not work, and the attackers threaten to carry out Denial of Service (DoS) attacks to disrupt the victim's services.
• Finally, quadruple extortion includes the threat of cybercriminals contacting customers, partners, victims' employees and the media to harass them and inform them about the data breach.
Case Study
The campaign named C0015 by Mitre Attack is a ransomware intrusion case where unidentified attackers used Bazar, Cobalt Strike and Conti, along with other tools, over five days.
Start of the Intrusion: The intrusion started with a BazarLoader infection, probably spread through a phishing campaign distributing password-protected zip files containing malicious documents.
Evolution to Conti: It is common for intrusions that start with BazarLoader to end with the deployment of Conti ransomware, as happened in this case.
Tools and Tactics: Tools such as net, nltest, ShareFinder, and Cobalt Strike were used for network discovery and command and control (C2). In addition, WMIC was used to expand access within the network.
Chronology of the Intrusion:
• First 2 hours Cobalt Strike and keyboard operators began gathering information about the network.
• Day 2 RDP was used to access the backup server and review its configuration.
• Day 4 Performed a second round of data exfiltration using Rclone and MEGA.
• Day 5 Deployed the Conti ransomware after attempting to dump the LSASS process and configure AnyDesk.
Current Panorama
As mentioned above, time is one of the most important factors to take into account, both on the cyberattacker's side to deploy the ransomware and on the victim's side to detect it. Companies such as Crowdstrike, Palo Alto and Cloudflare in their annual reports indicate that the time it takes cyberattackers is decreasing considerably year on year. Estimating what took weeks to accomplish a couple of years ago, today takes on average only a couple of days, and in some cases less time. This decrease in the time window that includes the entire ransomware campaign has come about in large part due to the incorporation of social engineering in the early stages of a ransomware campaign.
The Unit 42 team of Palo Alto in its Incident Response Report 2024, indicates that the difference between the speed between the compromise of a system and the exfiltration of the information obtained on average was around nine days in 2022. Currently, there have been cases where phishing has been used at the beginning of the cyberattack where this time has been shortened considerably, even not reaching 24 hours in total. In summary, it was seen that a group of cyberattackers affiliated to RaaS was operating in this way:
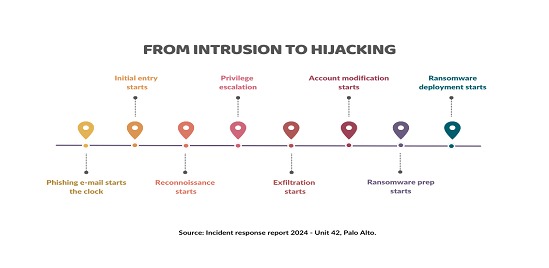
Regarding the first part of 2024, it was observed that the highest number of ransomware cyberattacks occurred in the month of February. At the same time, it was in that month that the highest ransom demand in history was recorded, consisting of 75 million dollars. Although the identity of the victim company has not been disclosed, it is known that the amount was paid.
It is estimated that the industries that suffered the most were factories, health services and construction, since the interruption of their services usually has a devastating impact. In the particular case of the health services industry, the type of information they protect is highly sensitive, making them especially vulnerable to double extortion methods.
Some of the means used to gain initial access to the compromised systems were: PDF files hosted on external URLs and HTML smuggling; WebDav files to distribute payloads; fake browser updates; ZIP files hosted on GitHub; Inno Setup and Clickonce installers that install RMM tools; Office files with hidden macros, among others.
The convergence between social engineering and ransomware creates a scenario where human vulnerability and technical coercion leverage each other, amplifying the impact of both. Sometimes, ransomware is the tool that is deployed after an attacker managed to sneak into a system through social engineering tactics.
In this context, it becomes imperative for companies to invest in training and preparing their employees to recognize and resist social engineering techniques. By strengthening the human link, organizations can significantly reduce the risk of falling into these traps, which could ultimately save them from suffering a ransomware attack and avoid devastating consequences.
Risk Mitigation Strategies
How to Detect Spear Phishing Attacks:
• E-mail address and sender's name: Check and verify the email address and sender's name, as many times attackers use spoofed addresses to impersonate someone trustworthy.
• Urgency and Pressure: Pay close attention if you receive a request and ask for an urgent action, attackers often put pressure on you not to verify the request and act without thinking.
• Suspicious Links and Files: Before clicking on a link, if you place the mouse over it you can see the real URL. The same with attachments; if you receive a file from someone you don't know or have nothing to do with, it is better to be suspicious.
• Rare Requests: If you are asked for sensitive information, unexpected payments or your account passwords, verify with the corresponding entity that the request is real. Although, for example, a bank will never ask you to send your credentials.
• Context and Timing: If the email arrives at an odd time or in an unrelated context, it could be a red flag. For example, outside the business hours of the supposed business/company they are contacting.
Recommendations Against Spear Phishing Attacks:
• Security training for users: ftraining employees, suppliers and other users to recognize phishing and social engineering attacks decreases the likelihood of a successful RaaS attack.
• Zero Trust Security: is a security model based on the premise of not automatically trusting anything inside or outside the corporate network, and constantly verifying all access attempts. It can mitigate the risk of ransomware and social engineering attacks by segmenting the network, implementing strict access controls, and requiring authentication and authorization for every access request.
• Email security: Email security solutions are sets of tools and technologies that are implemented to safeguard corporate email accounts against cyber-attacks. These solutions typically include spam filtering, malware detection and prevention, phishing protection, email encryption, secure archiving, and data retention policies, all to ensure the integrity, confidentiality and availability of electronic communications in the corporate environment.
• Back up data frequently: Ransomware renders organizations unable to access or use their data. But in many cases, an organization can restore its data from a backup rather than having to pay the ransom to decrypt it or rebuild its entire IT infrastructure from scratch.
• Use a SIEM (Security Information and Event Management): it detects anomalous behavior or signs of a ransomware infection, such as mass file encryption, and generates real-time alerts to enable a rapid response. In turn, it can correlate suspicious events, such as failed login attempts from unusual locations or anomalous activity on user accounts, enabling the identification and mitigation of exploit attempts resulting from social engineering attacks.
• Having visibility with an XDR (Extended Detection and Response): provides advanced threat detection at multiple points in the infrastructure (endpoints, emails, networks) and automates responses to contain and remediate ransomware infections before they spread. On the other hand, it enables unified visibility into suspicious activity across the organization, identifying patterns of behavior that could indicate a social engineering attack in progress, such as phishing attempts that compromise accounts or users behaving out of character.
• SOC (Security Operations Center): A SOC is a security team responsible for monitoring, detecting, analyzing and responding to cybersecurity incidents in real time. The SOC centralizes the organization's security oversight and proactively coordinates incident response. It is now possible to contract this type of solution so that it does not have to be implemented from scratch:
• Integration and Coordination: SIEM and XDR can be integrated within the SOC to provide a multi-layered defense. SIEM collects and analyzes large volumes of data, XDR extends detection to multiple environments, and SOC monitors and coordinates threat response.
• Early Detection and Rapid Response: Together, these technologies enable rapid detection and response to incidents, minimizing the impact of ransomware attacks and mitigating the consequences of social engineering attacks.
• Continuous Improvement: The SOC uses information provided by the SIEM and XDR to continuously improve security policies, train personnel and adjust configurations to better defend against future attacks.
Conclusion
The steady increase in ransomware attacks, especially those powered by social engineering techniques, makes clear the need for organizations to adopt comprehensive, multifaceted security approaches. Social engineering takes advantage of human vulnerabilities, allowing ransomware to break through traditional defenses and wreak significant havoc. With the evolution of ransomware to models such as Ransomware as a Service (RaaS), even attackers with little technical skill can carry out devastating attacks, using platforms that incorporate these techniques to save time and resources.
To effectively protect themselves, companies must implement a combination of advanced technologies such as SIEM, XDR and SOC, coupled with training and awareness strategies for their employees. It is important to note that not all companies need to build a SOC from scratch; there are specialized vendors that offer managed SOC services, providing access to world-class security monitoring and response without the need for a large upfront investment.
These tools and services not only enable early detection and response to incidents, but also provide a layered defense that significantly reduces the risk of successful ransomware and RaaS attacks. By integrating and coordinating these solutions, organizations can constantly improve their security posture, addressing today's threats and better preparing for those to come.