In the field of cybersecurity, it is common to adapt concepts and models from other disciplines to strengthen defense against cyber threats. Examples such as defense in depth in the military sector and risk management in financial sectors demonstrate this trend. "Cybersecurity exposure management" is another concept being introduced as a new area of study within Active Cyber Defense. CEM seeks to focus on identifying, analyzing and managing the risks to which an organization may be exposed, extending vulnerability and threat management practices to provide a more holistic approach through the lens of risk. In this post we hope to deepen the concepts already explored in a previous publication in which we have already begun to analyze people, processes and technologies related to SCM.
Analogy with the Immune System
The concept of ECM can be understood through an analogy with the human immune system. The immune system is the body's natural defense against infection and disease, and its functioning offers useful parallels for understanding how ECM protects an organization's digital assets.
Threat Identification and Assessment: Just as the immune system identifies and assesses pathogens that can cause infections, ECM focuses on identifying and assessing risks to information and data systems. The immune system recognizes harmful microorganisms such as viruses and bacteria, and classifies them according to their dangerousness. Similarly, SCM identifies vulnerabilities and cyber threats, categorizing them according to their potential impact and likelihood of exploitation.
Proactive and Preventive Response: The immune system acts proactively by detecting and neutralizing threats before they can cause significant harm. This includes the production of antibodies and activation of immune cells to fight infections. In parallel, the GEC implements proactive measures to reduce exposure and mitigate risks before they can be exploited by malicious actors. This involves the use of technologies and processes that continuously monitor, assess and prioritize vulnerability remediation.
Defense in Depth and Resilience: The immune system has multiple layers of defense, from physical barriers such as the skin to internal defenses such as T and B cells. These layers work together to provide a robust and resilient defense against infection. GEC takes a similar defense-in-depth approach, implementing multiple layers of security including firewalls, intrusion detection systems, and access controls, among others. In addition, it focuses on improving the resilience of systems by identifying and mitigating critical exposures.
Adaptive Response: The immune system is adaptive, adjusting and improving its response as it faces new threats. Through immunological memory, it can respond more quickly and effectively to recurrent infections. Similarly, SCM involves a continuous process of adaptation and improvement. Organizations use threat intelligence and attack simulations to constantly learn and improve their cyber defenses, ensuring they are prepared to respond to emerging threats effectively.
Integrating known functions
Beyond basic elements such as risk management, vulnerability management, SCM initially relies on the integration of other known functions and technologies to strengthen its definition. We can list here digital risk protection services (DRM), external attack surface management (EASM) and cyber asset attack surface management (CAASM). In addition, breach and attack simulation tools (BAS), automated penetration testing (CART) and vulnerability assessment and prioritization technologies (VA and VPT) are incorporated. These capabilities enable a holistic approach, providing a comprehensive view of the attack surface and facilitating proactive risk prioritization and mitigation. Consolidating these individual capabilities under GEC transforms the way the organization manages exposure, improving the overall security posture at the end of the day.
CEM vs. Vulnerability Management
CEM seeks to differentiate itself from traditional vulnerability management by focusing primarily on the conditions that enable threat actors to gain access through layered targeted attacks. This approach is based on the premise that while a vulnerability is a weakness exploited to gain unauthorized access, exposure refers to the conditions that facilitate such access (more akin to a weakness). CEM strives for threat exposure control, seeking to reduce attack opportunities through proactive and continuous risk management.
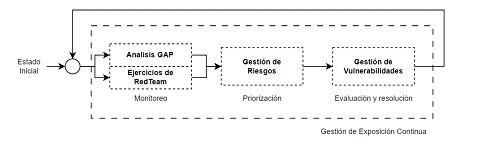
This approach is not new in itself; a set of processes and technologies is already proposed for this purpose, making it possible to continuously assess the visibility of digital assets and validate their accessibility and vulnerabilities. This approach is part of a Continuous Threat Exposure Management (CTEM) program, composed in principle of five stages:
Scope: Definition of the security perimeter and critical assets.
Discovery: Identification of all digital assets and their potential exposures.
Prioritization: Risk assessment and prioritization based on potential impact.
Validation: Verification of the effectiveness of controls through simulations and tests.
Mobilization: Effective implementation of responses and corrective measures.

We can highlight here the interrelationship between vulnerability, risk and resilience management, concluding that vulnerability reduction does not necessarily imply effective risk management. The importance of risk-based prioritization and process automation for efficient cybersecurity management is emphasized.
Benefits and Challenges of CEM Implementation
Improved cybersecurity decision-making: By having a clear understanding of the risk profile, resources can be allocated more strategically, focusing on areas that require priority attention.
Reducing the attack surface: By limiting the opportunities for attackers to exploit systems, the probability of successful attacks is reduced.
Optimizing cybersecurity priorities: Focusing efforts on areas of greatest risk and potential for harm ensures that resources are used where they are needed most.
Isolated view of vulnerabilities and exposure: Traditional vulnerability management tends to be done in silos, which limits the ability to understand the full risk picture. Addressing this challenge requires a holistic view of vulnerabilities as part of a whole.
Reactive approach: Many organizations still operate in a reactive manner, responding to incidents only after they occur rather than anticipating them.
Implementation complexity: Implementing an CEM program requires a strategic approach, including the mobilization of people and processes, and the integration of various technological tools. Good vulnerability management is not enough.
The adoption of SCM requires overcoming these challenges, usually through collaboration between different areas of the organization and using new methodologies (either with technology or services), to manage exposure on an ongoing basis.